 |
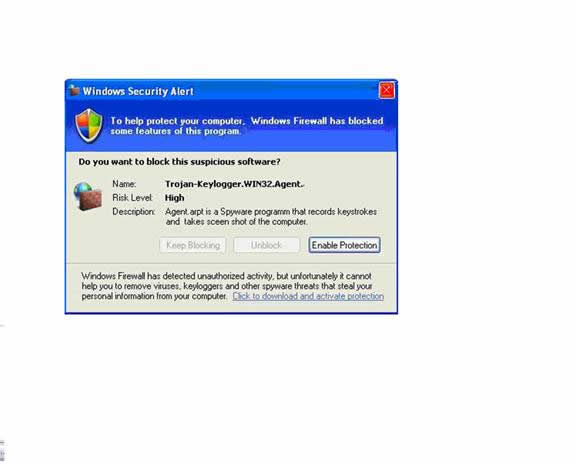
10) Recognizing a scareware.
This a phisher’s attempt to get your permission to install spyware.
How do you know its not real?
. 
Location
Background
Bad English
Appearance
Your security software has more permissions than you do, it doesn't’t need YOUR permission to download and activate software.
Any request that turn up while browsing asking you to turn
off your anti-virus, poke a hole in your firewall and run and install software
should be considered extremely dangerous. If you’re faced with any of
the warning signs of a scareware scam or suspect a problem, shut down your browser.
Don’t click "No" or "Cancel," or even the "x"
at the top right corner of the screen. Some scareware is designed so that any
of those buttons can activate the program. If you use Windows, press Ctrl +
Alt + Delete to open your Task Manager, and click "End Task." If you
use a Mac, press Command + Option + Q + Esc to "Force Quit."
SCAREWARE ARIVES VIA EMAIL TOO.
The teddy bear hoax is a good example.
I had a virus, but as you're on my address list this virus has probably forwarded itself on to you. It is easily removed if you don't open the file (jdbgmgr.exe) It has a teddy bear icon and is not detectable by norton or mcafee. First go to Start then the find or search option. In the files or folders option type jdbgmgr.exe. Search C drive and tick the 'include subfolders' and any other drives you may have. Click 'find now' - the virus has a gray teddy icon. DO NOT OPEN IT. Go to edit (on the menu bar) and 'select all'. Now go to file (on the menu bar) and DELETE. This will send it to the recycle bin so then go and delete or empty it there as well. If you find the virus (as I did!) you must contact everyone in your address book and send them these instructions. ASAP. Send this to everyone on your address list. |
![]()
An email like this can trick unwary computer users into deleting "jdbgmgr.exe", a legitimate Windows file.
While this was a harmless hoax, you can see how a malicious threat could be passed on just as easily.
Always check out emails you suspect to be hoaxes on Snopes.com or a similar site.
| Prev | Next |